Client Overview
Our client is a growing professional services business that relies heavily on email for day-to-day operations, client communication, and internal coordination. Like many organisations, they assumed that “no news is good news” when it came to cybersecurity.
Before we started working together, their view of email security was summed up in one sentence:
“I never hear that anything is happening to my domain, so I just assumed everything was fine.”
This is a common and dangerous mindset: no visible incidents ≠ no threats. In reality, it usually means threats are not being seen, not that they don’t exist.
The Challenge: Invisible Email Threats

When we first engaged with the client, they had:
- No clear visibility into who was sending email on behalf of their domain
- No centralised reporting on suspicious or malicious email traffic
- No proactive blocking of known bad actors or blacklisted IPs
- A belief that “if something was wrong, someone would tell us”
The risk here was twofold:
- Brand and domain abuse – Attackers could attempt to send phishing or spoofed emails pretending to be the client.
- Silent reputation damage – Blacklisted IPs and malicious senders could harm the domain’s reputation, impacting deliverability and trust.
Our goal was simple but critical:
Make email threats visible, measurable, and block them before they ever reach the client’s environment.
Our Approach: Visibility First, Then Control
We implemented a security-first email protection strategy focused on:
- Deep visibility into email sources
- Identifying all IP addresses sending email on behalf of the domain
- Distinguishing legitimate infrastructure from suspicious or blacklisted sources
- Blacklist and threat intelligence enforcement
- Cross-checking sending IPs against known threat intelligence and blacklists
- Automatically blocking or quarantining traffic from malicious sources
- Continuous monitoring and reporting
- Providing clear, ongoing metrics so the client could see exactly what was being blocked and why
Key Metrics: Before vs After
Once the solution was in place and monitoring began, we quickly uncovered what had previously been invisible.
Source IP Addresses
- 18 total IP addresses were seen sending email related to the client’s domain
- 15 of those IP addresses were blacklisted
- 0 potential threats were allowed through once controls were active
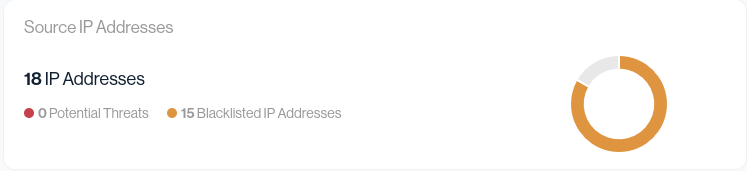
This means that the majority of IPs touching the domain were not trustworthy – but they were being silently ignored before we stepped in.
Email Volume
Over the measured period, we observed:
- 42 total emails associated with the domain
- 38 emails came from blacklisted IP addresses
- 0 volume from threats reached the client’s inbox
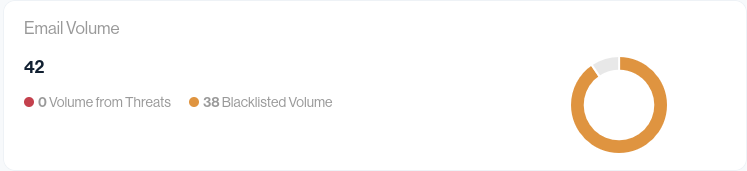
In other words, over 90% of the observed email volume was coming from blacklisted sources, yet the client had no idea this was happening.
What This Actually Means in Practice
Without proper visibility and controls, those 38 emails from blacklisted IPs could have been:
- Phishing attempts targeting staff or customers
- Spoofed emails pretending to be from the client’s domain
- Malicious messages designed to harvest credentials or deliver malware
With our controls in place:
- All 15 blacklisted IPs are identified and treated as hostile
- All 38 emails from those blacklisted IPs are blocked or neutralised
- The client sees 0 threats in their inbox – not because nothing is happening, but because everything is being stopped upstream
This is the crucial shift:
From “we never hear anything” to “we know exactly what’s happening, and we’re stopping it.”
The Client’s Perspective: Before and After
Before
The client’s original mindset was:
“I never hear that anything is happening to my domain, so I just assumed everything was fine. We didn’t have any obvious incidents, so email security wasn’t really on my radar.”
This is a textbook example of security by assumption, not by design.
After Implementation
Once we shared the real data – 18 IPs, 15 blacklisted, 38 blacklisted emails blocked – their view changed dramatically:
“Seeing the reports was a wake-up call. I genuinely thought nothing was happening because no one complained. Now I can see how many bad sources were trying to use or abuse our domain, and I’m relieved that it’s being actively blocked before it reaches us or our clients.”
The client went from unaware and unprotected to informed and proactively defended.
Business Impact
The improvements are not just technical; they have direct business value:
- Brand Protection
- Reduced risk of attackers impersonating the company via email
- Stronger trust with clients who rely on email communication
- Reduced Risk of Compromise
- Blacklisted IPs and suspicious senders are blocked before they can deliver phishing or malware
- Lower likelihood of account takeovers and data breaches originating from email
- Improved Domain Reputation
- Cleaner sending profile and reduced association with malicious traffic
- Better deliverability for legitimate business emails
- Actionable Visibility
- Clear metrics on IP sources, blacklisted activity, and blocked volume
- The client can now see, in numbers, how their risk has been reduced
Summary: From Assumption to Assurance
This case shows a pattern we see often:
- Before: “We never hear about problems, so we must be fine.”
- After: “We can see the threats, measure them, and prove they’re being blocked.”
With:
- 18 source IPs identified
- 15 blacklisted IPs flagged and controlled
- 42 total emails analysed
- 38 emails from blacklisted IPs blocked
- 0 threats delivered to the client’s inbox
…the client’s email security posture has moved from reactive and blind to proactive, measurable, and defensible.
If your current view of email security is still “I don’t hear about any problems, so I guess we’re okay,” this case is a strong indicator that it’s time to get real visibility into what’s actually happening to your domain—and to start blocking threats before they become incidents.

No responses yet